Deploy a ROSA HCP Cluster with Terraform
This guide provides a detailed tutorial for deploying a Red Hat OpenShift on AWS (ROSA) cluster with Hosted Control Plane (HCP) capabilities. It is specifically tailored for deploying Camunda 8 using Terraform, a widely-used Infrastructure as Code (IaC) tool.
We recommend this guide for building a robust and sustainable infrastructure. However, if you are looking for a quicker trial or proof of concept, or if your needs aren't fully met by our module, consider following the official ROSA Quickstart Guide.
This guide aims to help you leverage IaC to streamline and reproduce your cloud infrastructure setup. While it covers the essentials for deploying an ROSA HCP cluster, for more advanced use cases, please refer to the official Red Hat OpenShift on AWS Documentation.
If you are completely new to Terraform and the idea of IaC, read through the Terraform IaC documentation and give their interactive quick start a try for a basic understanding.
Requirements
- A Red Hat Account to create the Red Hat OpenShift cluster.
- An AWS account to create any resources within AWS.
- AWS CLI, a CLI tool for creating AWS resources.
- Terraform
- kubectl to interact with the cluster.
- ROSA CLI to interact with the cluster.
- jq to interact with some Terraform variables.
- This guide uses GNU/Bash for all the shell commands listed.
For the tool versions used, check the .tool-versions file in the repository. It contains an up-to-date list of versions that we also use for testing.
Considerations
This setup provides a foundational starting point for working with Camunda 8, though it is not optimized for peak performance. It serves as a solid initial step in preparing a production environment by leveraging Infrastructure as Code (IaC) tools.
Terraform can initially appear complex. If you're new to it, you might want to start by considering trying out the Red Hat OpenShift on AWS UI-based tutorial. This guide will show you what resources are created and how they interact with each other.
If you require managed services for PostgreSQL Aurora or OpenSearch, you can refer to the definitions provided in the EKS setup with Terraform guide. However, please note that these configurations may need adjustments to fit your specific requirements and have not been tested. By default, this guide assumes that the database services (PostgreSQL and Elasticsearch) integrated into the default chart will be used.
For testing Camunda 8 or developing against it, you might consider signing up for our SaaS offering. If you already have a Red Hat OpenShift cluster on AWS, you can skip ahead to the Helm setup guide.
To keep this guide concise, we provide links to additional documentation covering best practices, allowing you to explore each topic in greater depth.
Following this guide will incur costs on your cloud provider account and your Red Hat account, specifically for the managed OpenShift service, OpenShift worker nodes running in EC2, the hosted control plane, Elastic Block Storage (EBS), and Route 53. For more details, refer to ROSA AWS pricing and the AWS Pricing Calculator as total costs vary by region.
Variants
Unlike the EKS Terraform setup, we currently support only one main variant of this setup:
-
The standard installation uses a username and password connection for Camunda components (or relies solely on network isolation for certain components). This option is straightforward and easier to implement, making it ideal for environments where simplicity and rapid deployment are priorities, or where network isolation provides adequate security.
-
The second variant, IRSA (IAM Roles for Service Accounts), may work but has not been tested. If you’re interested in setting it up, please refer to the EKS guide as a foundational resource.
Outcome
Infrastructure diagram for a single region ROSA setup (click on the image to open the PDF version)
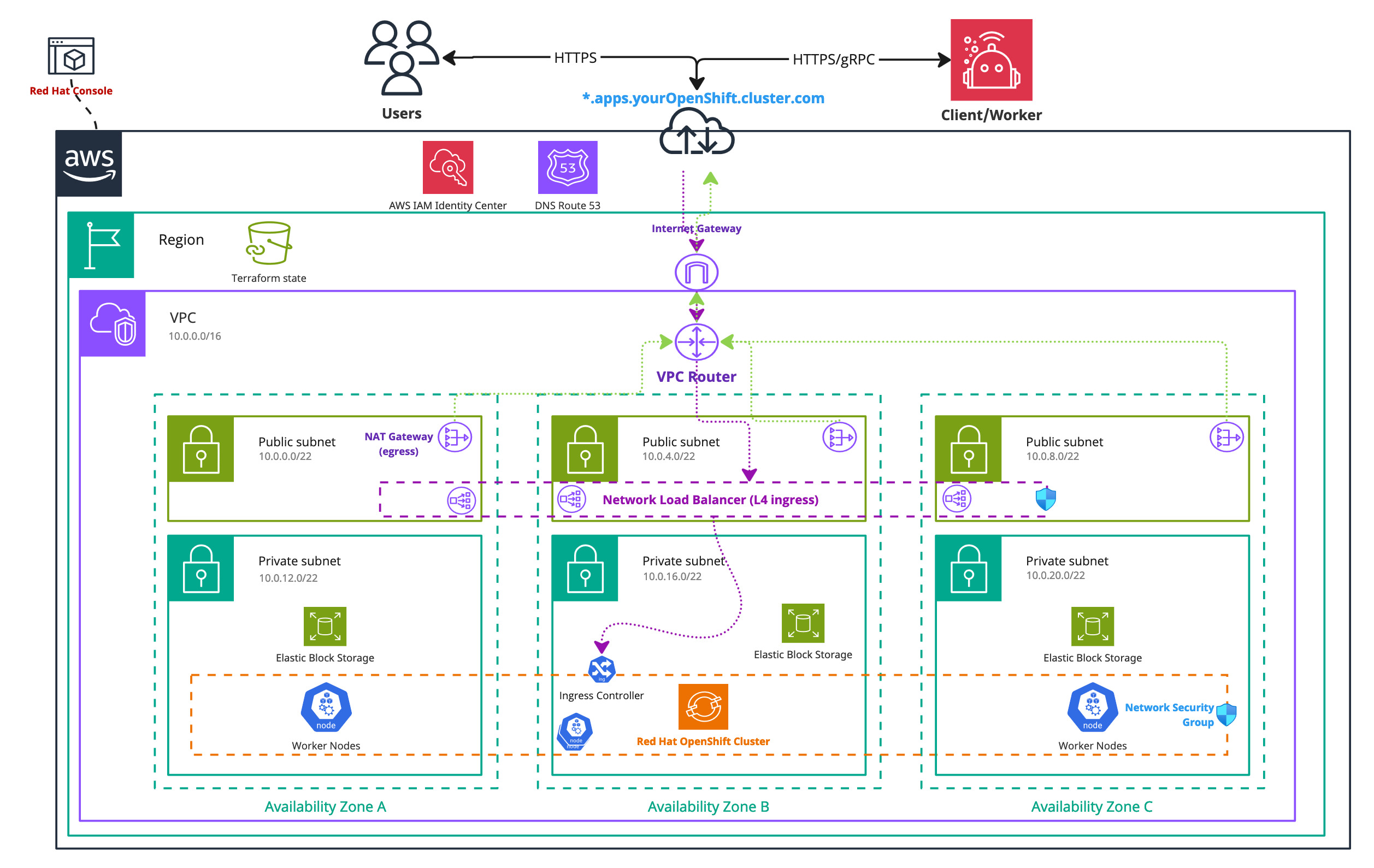
Following this tutorial and steps will result in:
- A Red Hat OpenShift with Hosted Control Plane cluster running the latest ROSA version with six nodes ready for Camunda 8 installation.
- The EBS CSI driver is installed and configured, which is used by the Camunda 8 Helm chart to create persistent volumes.
1. Configure AWS and initialize Terraform
Obtain a copy of the reference architecture
The first step is to download a copy of the reference architecture from the GitHub repository. This material will be used throughout the rest of this documentation, the reference architecture is versioned using the same Camunda versions (stable/8.x).
loading...
With the reference architecture copied, you can proceed with the remaining steps outlined in this documentation. Ensure that you are in the correct directory before continuing with further instructions.
Terraform prerequisites
To manage the infrastructure for Camunda 8 on AWS using Terraform, we need to set up Terraform's backend to store the state file remotely in an S3 bucket. This ensures secure and persistent storage of the state file.
Advanced users may want to handle this part differently and use a different backend. The backend setup provided is an example for new users.
Set up AWS authentication
The AWS Terraform provider is required to create resources in AWS. Before you can use the provider, you must authenticate it using your AWS credentials.
A user who creates resources in AWS will always retain administrative access to those resources, including any Kubernetes clusters created. It is recommended to create a dedicated AWS IAM user for Terraform purposes, ensuring that the resources are managed and owned by that user.
You can further change the region and other preferences and explore different authentication methods:
-
For development or testing purposes you can use the AWS CLI. If you have configured your AWS CLI, Terraform will automatically detect and use those credentials. To configure the AWS CLI:
aws configureEnter your
AWS_ACCESS_KEY_ID,AWS_SECRET_ACCESS_KEY, region, and output format. These can be retrieved from the AWS Console. -
For production environments, we recommend the use of a dedicated IAM user. Create access keys for the new IAM user via the console, and export them as
AWS_ACCESS_KEY_IDandAWS_SECRET_ACCESS_KEY.
Create an S3 bucket for Terraform state management
Before setting up Terraform, you need to create an S3 bucket that will store the state file. This is important for collaboration and to prevent issues like state file corruption.
To start, set the region as an environment variable upfront to avoid repeating it in each command:
export AWS_REGION=<your-region>
Replace <your-region> with your chosen AWS region (for example, eu-central-1).
Now, follow these steps to create the S3 bucket with versioning enabled:
-
Open your terminal and ensure the AWS CLI is installed and configured.
-
Run the following command to create an S3 bucket for storing your Terraform state. Make sure to use a unique bucket name and set the
AWS_REGIONenvironment variable beforehand:# Replace "my-rosa-tf-state" with your unique bucket name
export S3_TF_BUCKET_NAME="my-rosa-tf-state"
export S3_TF_BUCKET_REGION="<your-region>"
aws s3api create-bucket --bucket "$S3_TF_BUCKET_NAME" --region "$S3_TF_BUCKET_REGION" \
--create-bucket-configuration LocationConstraint="$S3_TF_BUCKET_REGION"
Replace <your-region> with the AWS region where you want to create the S3 bucket (e.g., us-east-2).
This region can be different from the regions used for other resources, but it requires to be set explicitly in the backend configuration using the flag: -backend-config="region=<your-region>".
For clarity, this guide explicitly sets the bucket region in all relevant commands.
Steps to create the S3 bucket with versioning enabled:
-
Enable versioning on the S3 bucket to track changes and protect the state file from accidental deletions or overwrites:
aws s3api put-bucket-versioning --bucket "$S3_TF_BUCKET_NAME" --versioning-configuration Status=Enabled --region "$S3_TF_BUCKET_REGION" -
Secure the bucket by blocking public access:
aws s3api put-public-access-block --bucket "$S3_TF_BUCKET_NAME" --public-access-block-configuration \
"BlockPublicAcls=true,IgnorePublicAcls=true,BlockPublicPolicy=true,RestrictPublicBuckets=true" --region "$S3_TF_BUCKET_REGION" -
Verify versioning is enabled on the bucket:
aws s3api get-bucket-versioning --bucket "$S3_TF_BUCKET_NAME" --region "$S3_TF_BUCKET_REGION"
This S3 bucket will now securely store your Terraform state files with versioning enabled.
OpenShift cluster module setup
This module sets up the foundational configuration for ROSA HCP and Terraform usage.
We will leverage Terraform modules, which allow us to abstract resources into reusable components, simplifying infrastructure management.
The Camunda-provided module is publicly available and serves as a robust starting point for deploying a Red Hat OpenShift cluster on AWS using a Hosted Control Plane. It is highly recommended to review this module before implementation to understand its structure and capabilities.
This module is based on the official ROSA HCP Terraform module documentation. It is presented as an example for running Camunda 8 in ROSA.
For production or advanced use cases or custom setups, we encourage you to use the official module, which includes vendor-supported features.
Set up ROSA authentication
To set up a ROSA cluster, certain prerequisites must be configured on your AWS account. Below is an excerpt from the official ROSA planning prerequisites checklist:
-
Verify that your AWS account is correctly configured:
aws sts get-caller-identity -
Check if the ELB service role exists, as if you have never created a load balancer in your AWS account, the role for Elastic Load Balancing (ELB) might not exist yet:
aws iam get-role --role-name "AWSServiceRoleForElasticLoadBalancing"If it doesn't exist, create it:
aws iam create-service-linked-role --aws-service-name "elasticloadbalancing.amazonaws.com" -
Create a Red Hat Hybrid Cloud Console account if you don’t already have one: Red Hat Hybrid Cloud Console.
-
Enable ROSA on your AWS account via the AWS Console.
-
Enable HCP ROSA on AWS Marketplace:
- Navigate to the ROSA console: AWS ROSA Console.
- Choose Get started.
- On the Verify ROSA prerequisites page, select I agree to share my contact information with Red Hat.
- Choose Enable ROSA.
Note: Only a single AWS account can be associated with a Red Hat account for service billing.
-
Install the ROSA CLI from the OpenShift AWS Console.
-
Get an API token, go to the OpenShift Cluster Management API Token, click Load token, and save it. Use the token to log in with ROSA CLI:
export RHCS_TOKEN="<yourToken>"
rosa login --token="$RHCS_TOKEN"
# Verify the login
rosa whoami -
Verify your AWS quotas:
rosa verify quota --region="$AWS_REGION"Note: This may fail due to organizational policies.
-
Create the required account roles:
rosa create account-roles --mode auto -
Verify your AWS quotas, and if quotas are insufficient, consult the following:
- Ensure the
ocCLI is installed. If it’s not already installed, follow the official ROSA oc installation guide:
rosa verify openshift-client
Set up the ROSA cluster module
-
Ensure you are in the reference architecture directory of the cloned repository:
./aws/openshift/rosa-hcp-single-region/terraform/. Then, navigate into theclustermodule:ls
# Example output:
# cluster vpn
cd cluster -
Review the module configuration file
config.tf. This configuration will use the previously created S3 bucket for storing the Terraform state file:aws/openshift/rosa-hcp-single-region/terraform/cluster/config.tfloading... -
Edit the
cluster.tffile in the same directory as yourconfig.tffile:Configure your clusterCustomize the cluster name, availability zones, with the values you previously retrieved from the Red Hat Console. Additionally, provide a secure username and password for the cluster administrator.
Ensure that you have set the environment variable
RHCS_TOKENwith your OpenShift Cluster Management API Token.Private clusterBy default, this cluster is accessible from the internet. If you prefer to restrict access, set
locals.rosa_private_cluster = true. This will create a private cluster that is only accessible through the private subnets of your VPC. Optionally, you can still expose a public ingress: learn more.⚠️ Since private subnets are not reachable from the internet, you'll need to establish a connection between your network and the cluster. This can be done using a bastion host or a Client VPN.
The next section will guide you through setting up an AWS VPN Endpoint, which allows secure access to the private cluster.
aws/openshift/rosa-hcp-single-region/terraform/cluster/cluster.tfloading...Camunda Terraform moduleThis ROSA module is based on the official Red Hat Terraform module for ROSA HCP. Please be aware of potential differences and choices in implementation between this module and the official one.
We invite you to consult the Camunda ROSA module documentation for more information.
-
After setting up the terraform files and ensuring your AWS authentication is configured, initialize your Terraform project, then, initialize Terraform to configure the backend and download necessary provider plugins:
export S3_TF_BUCKET_KEY_CLUSTER="camunda-terraform/cluster.tfstate"
echo "Storing cluster terraform state in s3://$S3_TF_BUCKET_NAME/$S3_TF_BUCKET_KEY_CLUSTER"
terraform init -backend-config="bucket=$S3_TF_BUCKET_NAME" -backend-config="key=$S3_TF_BUCKET_KEY_CLUSTER" -backend-config="region=$S3_TF_BUCKET_REGION"Terraform will connect to the S3 bucket to manage the state file, ensuring remote and persistent storage.
-
Configure user access to the cluster. By default, the user who creates the OpenShift cluster has administrative access. If you want to grant access to other users, follow the Red Hat documentation for granting admin rights to users when the cluster is created.
-
Customize the cluster setup. The module offers various input options that allow you to further customize the cluster configuration. For a comprehensive list of available options and detailed usage instructions, refer to the ROSA module documentation.
Define outputs
Terraform allows you to define outputs, which make it easier to retrieve important values generated during execution, such as cluster endpoints and other necessary configurations for Helm setup.
Each module that you have previously set up contains an output definition at the end of the file. You can adjust them to your needs.
Execution
We strongly recommend managing sensitive information (for example, the administrator username and password) using a secure secrets management solution like HashiCorp Vault. For details on how to inject secrets directly into Terraform via Vault, see the Terraform Vault Secrets Injection Guide.
-
Plan the configuration files:
terraform plan -out cluster.plan # describe what will be created -
After reviewing the plan, you can confirm and apply the changes.
terraform apply cluster.plan # creates the resources
Terraform will now create the OpenShift cluster with all the necessary configurations. The completion of this process may require approximately 20-30 minutes for each component.
VPN module setup
This section guides you through setting up an AWS VPN Endpoint to access a private cluster.
This step is optional and only necessary if you have configured a private cluster.
Using a VPN offers a flexible and secure way to connect to the private subnets within your VPC. It can be used either by a user to access cluster resources or to enable cross-site communications via PrivateLink. This module focuses on user access.
Infrastructure diagram for a single region ROSA setup with VPN (click on the image to open the PDF version)
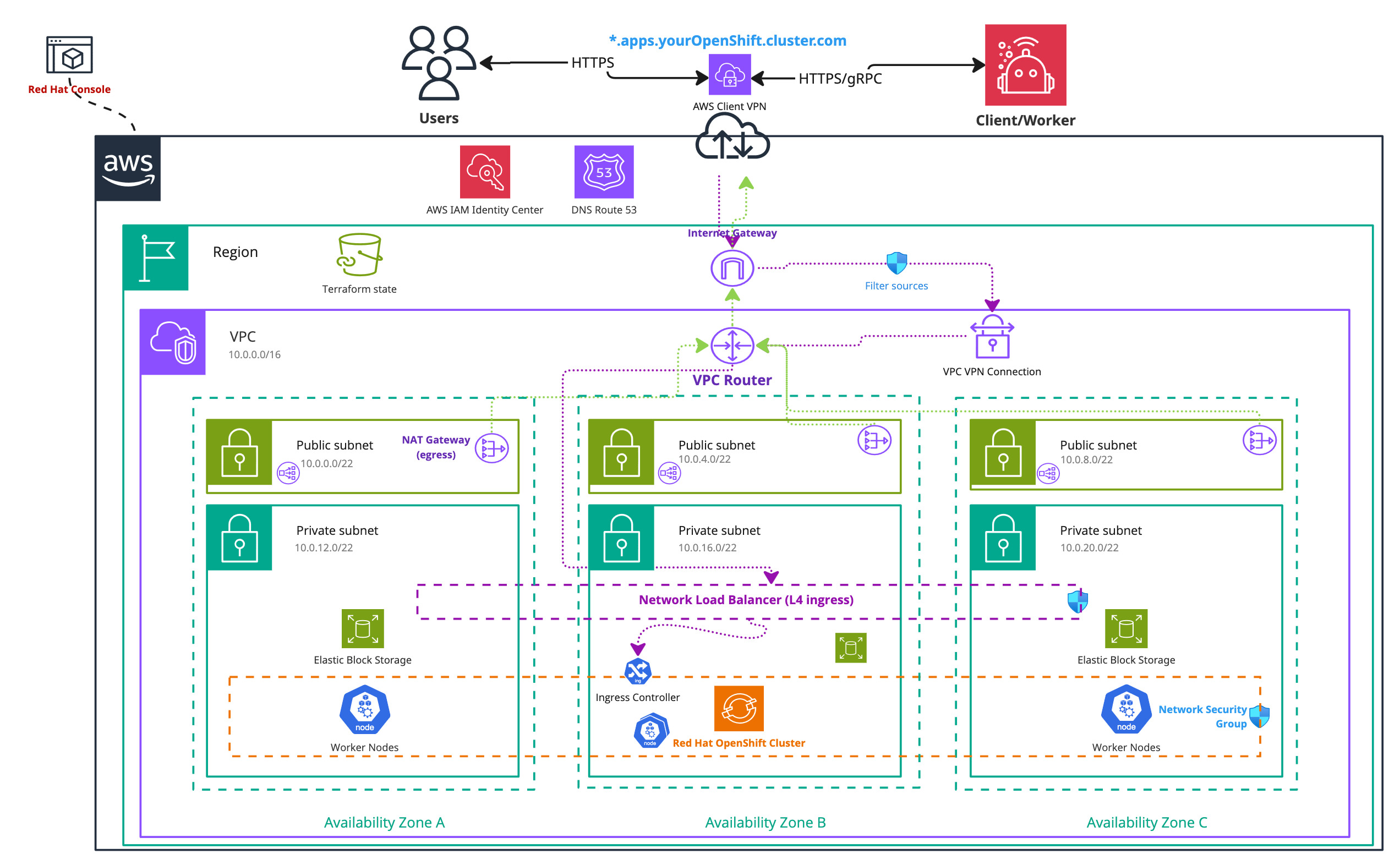
AWS VPN technology is compatible with OpenVPN clients. It uses x509 certificates for mutual authentication and source verification. The encryption provided by these certificates ensures that traffic can securely transit over the internet to the AWS VPN endpoint, which performs NAT and routes the traffic directly into the private subnets. This VPN endpoint thus becomes the sole access point to the private cluster.
Retrieve the VPC cluster ID
To create the VPN Endpoint in your cluster’s VPC, you need to retrieve the VPC ID using Terraform outputs from the OpenShift cluster module. Follow these steps:
-
Ensure you are in the reference architecture directory of the cloned repository:
./aws/openshift/rosa-hcp-single-region/terraform/. Navigate to theclustermodule directory inside your reference architecture repository, for example:ls
# Example output:
# cluster vpn
cd cluster -
Export the VPC ID to an environment variable:
export CLUSTER_VPC_ID="$(terraform output -raw vpc_id)"
echo "CLUSTER_VPC_ID=$CLUSTER_VPC_ID"
Set up the VPN module
From the parent directory containing your cluster module, go to the vpn directory which holds the VPN endpoint configuration.
This setup creates a Certificate Authority (CA) for AWS VPN to perform encryption and mutual client authentication. For simplicity, the CA and generated certificates are stored in the project’s Terraform state (tfstate). You may customize this as needed.
Start by reviewing the config.tf file that configures the S3 backend for Terraform state management:
loading...
Then, review vpn.tf, which describes the VPC Client Endpoint configuration:
loading...
This VPN Client Endpoint follows AWS best practices and constraints:
- Uses a client CIDR range that does not overlap with the VPC CIDR or any manually added VPN route table routes.
- Implements split-tunnel routing, so only traffic destined for the VPC goes through the VPN, minimizing bandwidth use.
- Supports IPv4 only and is bound to the VPC’s private subnets.
-
Set your Terraform state key and initialize Terraform with the S3 backend and download necessary provider plugins:
export S3_TF_BUCKET_KEY_VPN="camunda-terraform/vpn.tfstate"
echo "Storing cluster terraform state in s3://$S3_TF_BUCKET_NAME/$S3_TF_BUCKET_KEY_VPN"
terraform init -backend-config="bucket=$S3_TF_BUCKET_NAME" -backend-config="key=$S3_TF_BUCKET_KEY_VPN" -backend-config="region=$S3_TF_BUCKET_REGION"Terraform will connect to the S3 bucket to manage the state file, ensuring remote and persistent storage.
-
For each client connecting to the cluster, assign a unique name in
client_key_namesto simplify certificate revocation. -
By default, VPN access is allowed from any IP address. You may restrict access by adjusting the
vpn_allowed_cidr_blocksvariable. -
Network designs vary; please review and adjust the configuration to fit your topology.
-
Customize the VPN module by referring to the VPN module documentation.
Outputs
The module stores certificates and VPN client configurations in the Terraform state. The next section explains how to retrieve and use client configurations.
Execution
-
Generate a Terraform plan for the VPN Client Endpoint configuration. This will use the private subnets of the designated VPC:
# describe what will be created
terraform plan -out vpn.plan \
-var vpc_id="$CLUSTER_VPC_ID" -
Review and apply the plan to create the resources:
terraform apply vpn.plan # creates the resources
Creation of the VPN Client Endpoint typically takes about 10 minutes. After completion, the client configurations will be available in the Terraform output vpn_client_configs.
Reference files
Depending on the installation path you have chosen, you can find the reference files used on this page:
- Standard installation: Reference Files
2. Preparation for Camunda 8 installation
Access to the private network using the VPN
This section applies if you have previously created a private cluster and want to access it using the VPN module configured earlier.
-
Navigate to the VPN module directory (
vpn):pwd
# Example output:
# ./camunda-deployment-references/aws/openshift/rosa-hcp-single-region/terraform/vpn/ -
Generate your client’s VPN configuration file. This file is compatible with OpenVPN (ovpn) format:
aws/openshift/rosa-hcp-single-region/procedure/gather-vpn-config.shloading... -
Import the generated configuration file (
my-client.ovpn) into an OpenVPN client:- (preferred) Official AWS VPN Client
- Other OpenVPN Clients
-
Once the VPN client is connected, you will have secure access to the VPC’s private network.
Access the created OpenShift cluster
You can access the created OpenShift cluster using the following steps:
-
Verify that you are in the OpenShift clusters module directory
clusters:pwd
# Example output:
# ./camunda-deployment-references/aws/openshift/rosa-hcp-single-region/terraform/cluster/ -
Set up the required environment variables from the OpenShift terraform module:
aws/openshift/rosa-hcp-single-region/procedure/gather-cluster-login-id.shloading... -
If you want to give cluster administrator access to the created user, this is not required for a standard installation but can be useful for debugging:
rosa grant user cluster-admin --cluster="$CLUSTER_NAME" --user="$CLUSTER_ADMIN_USERNAME" -
Log in to the OpenShift cluster:
oc login -u "$CLUSTER_ADMIN_USERNAME" "$CLUSTER_API_URL" -p "$CLUSTER_ADMIN_PASSWORD"Clean up and configure the kubeconfig context:
oc config rename-context $(oc config current-context) "$CLUSTER_NAME"
oc config use-context "$CLUSTER_NAME" -
Verify your connection to the cluster with
oc:oc get nodes -
Create a project for Camunda using
oc:oc new-project camundaIn the remainder of the guide, the
camundanamespace part of the camunda project will be referenced to create the required resources in the Kubernetes cluster, such as secrets or one-time setup jobs.
3. Install Camunda 8 using the Helm chart
Now that you've exported the necessary values, you can proceed with installing Camunda 8 using Helm charts. Follow the guide Camunda 8 on OpenShift for detailed instructions on deploying the platform to your OpenShift cluster.