Flags
Flags allow you to control the availability of certain features within Desktop Modeler.
Configuring Flags
You may configure flags in a flags.json file or pass them via CLI.
Configure in flags.json
Place a flags.json file inside the resources folder of your local {USER_DATA} or {APP_DATA_DIRECTORY} directory to persist them.
Configure via CLI
Pass flags via the command line when starting the application.
- Windows
- macOS
- Linux
"Camunda Modeler.exe" --disable-plugins
camunda-modeler --disable-plugins
camunda-modeler --disable-plugins
Flags passed as command line arguments take precedence over those configured via a configuration file.
Available Flags
| flag | default value |
|---|---|
| "disable-plugins" | false |
| "disable-adjust-origin" | false |
| "disable-cmmn" | true |
| "disable-dmn" | false |
| "disable-form" | false |
| "disable-platform" | false |
| "disable-zeebe" | false |
| "disable-remote-interaction" | false |
| "single-instance" | false |
| "user-data-dir" | Electron default |
| "display-version" | undefined |
| "zeebe-ssl-certificate" | undefined |
| "c7-engine-version" | undefined |
| "c8-engine-version" | undefined |
Examples
Disable Plug-ins
Start the modeler without activating installed plug-ins. This is useful to debug modeler errors.
BPMN-only Mode
To disable the DMN and Form editing capabilities of the App, configure your flags.json like this:
{
"disable-dmn": true,
"disable-form": true
}
As a result, the app will only allow users to model BPMN diagrams.
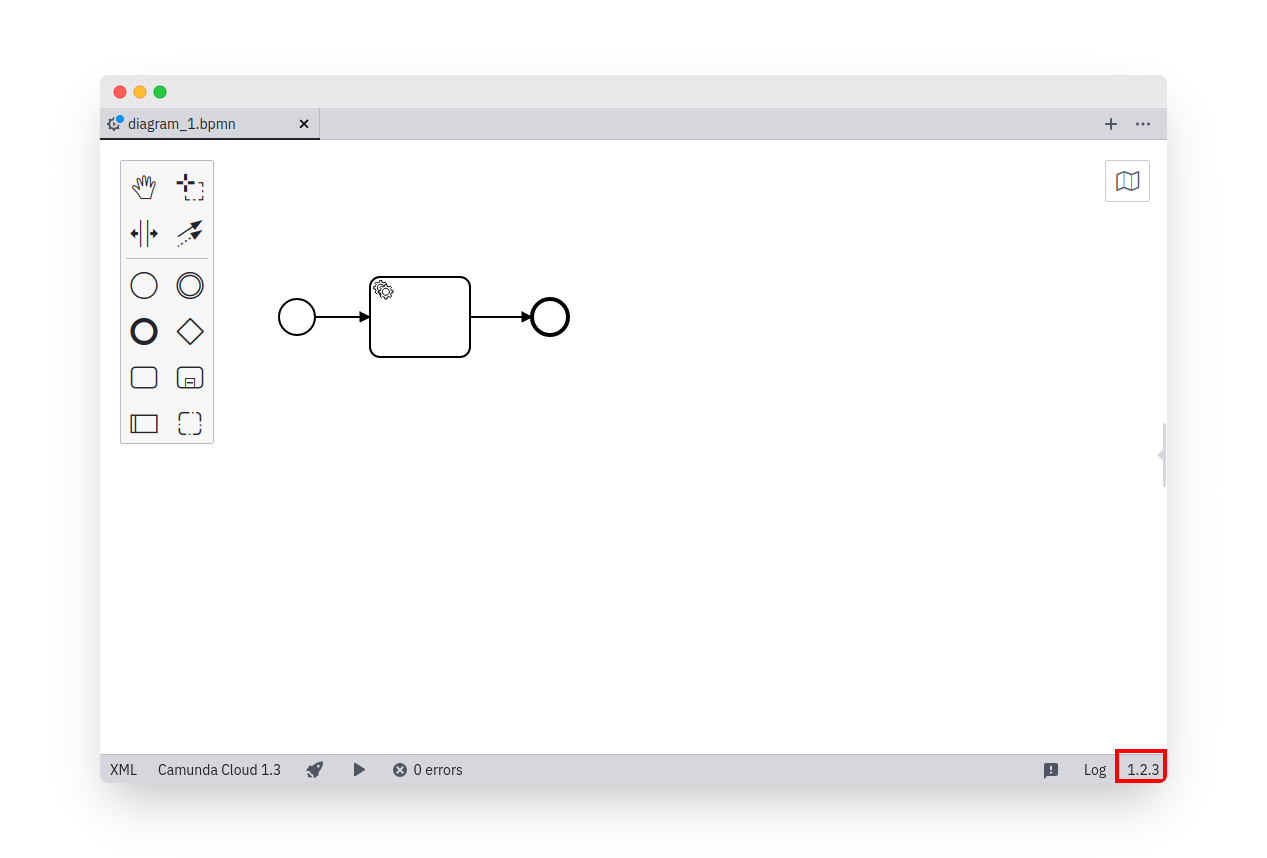
Custom display-version label
To display a custom version information in the status bar of the app, configure your flags.json like this:
{
"display-version": "1.2.3"
}
Zeebe SSL certificate
ℹ️ The Modeler will read trusted certificates from your operating system's trust store.
Provide additional certificates to validate secured connections to a Camunda 8 installation.
Configure your flags.json like this:
{
"zeebe-ssl-certificate": "C:\\path\\to\\certs\\trusted-custom-roots.pem"
}
Additional information adapted from the upstream documentation:
The peer (Camunda 8) certificate must be chainable to a CA trusted by the app for the connection to be authenticated. When using certificates that are not chainable to a well-known CA, the certificate's CA must be explicitly specified as trusted or the connection will fail to authenticate. If the peer uses a certificate that doesn't match or chain to one of the default CAs, provide a CA certificate that the peer's certificate can match or chain to. For self-signed certificates, the certificate is its own CA, and must be provided.
Default execution platform version
To change default execution platform version, configure your flags.json as follows:
{
"c7-engine-version": "7.18.0",
"c8-engine-version": "8.0.0"
}
New diagrams created in Desktop Modeler will use the configured version instead of the latest stable version.